I’m considering switching my remote backups to S3 from a syncing service, as using a file syncing service seems to be the less efficient solution. However, I am having some trouble understanding how encryption works when using a S3 service, and would appreciate some help wrapping my head around it. Here is what I have done and (think) I understand thus far:
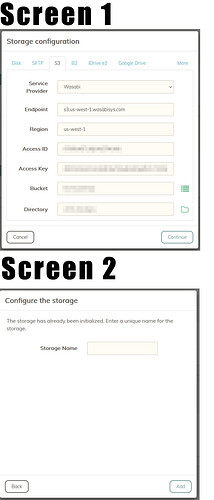
I set up a test bucked on Wasabi, created a duplicacy storage (via web ui), and ran a backup. When looking at the files on Wasabi, it seems clear the chunks are encrypted. So far so good, but I need help understanding how these files were encrypted.
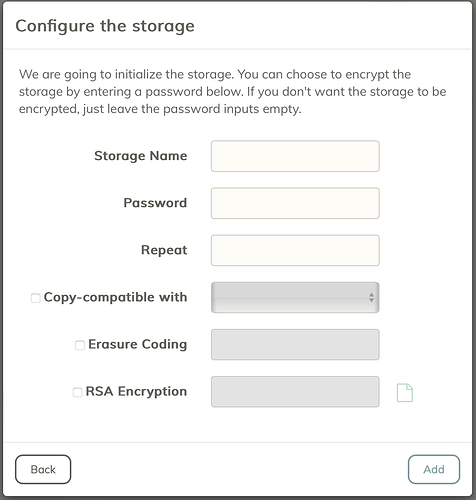
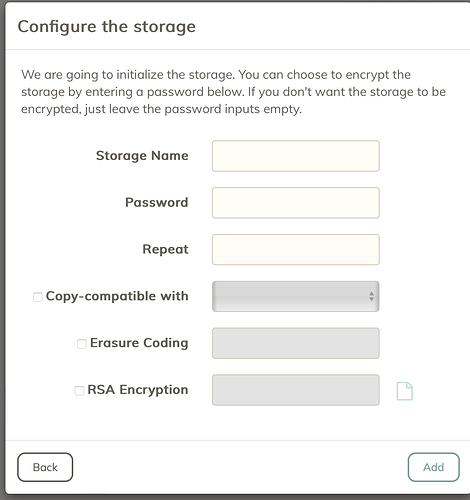
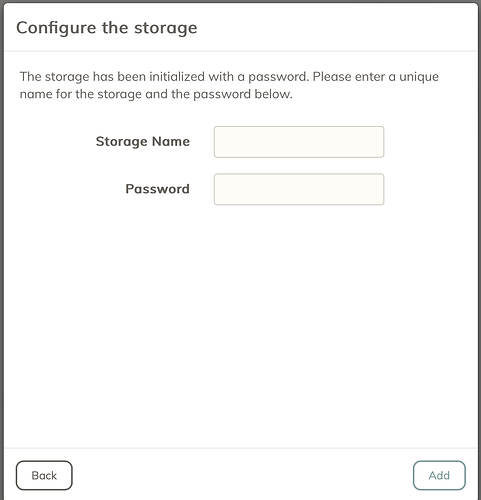
When you set up a local storage, you are prompted for a password which will form the basis of the encryption (to my understanding), but there is no such option when using S3. My first guess is that the secret key is used to encrypt files when sending them to S3. However, given the secret key was generated by the S3 provider, does that mean they could decrypt my files? Or does duplicacy incorporate some other component?
At first I thought some element of the config files may be used, but was able to send a backup on one machine, and restore it on another (which presumably has somewhat different config file contents). I used the same master password for both machines though, so maybe that is the other element?
If someone could help fill in the gaps/correct my misunderstandings here it would be helpful.
For context, I have been using Duplicati to send files via rsync to my local server & pcloud, and am looking for other solutions. Any input would be appreciated. Thank you!