It absolutely does:
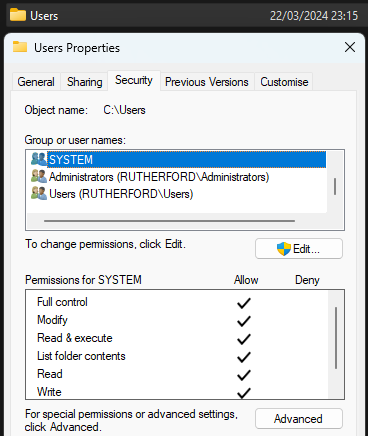
Practically most folders on a Windows OS have full perms for the SYSTEM account, hence why most services use said account.
On my personal PC I run Duplicacy on manual startup (no service mode and installed for just my user account), so I have to modify the shortcut to Run as admin.
On my brother’s PC he runs Duplicacy as a service (installed for all users) and it’s backing up C:\Users\<username>, but I modified the service account to a custom account .\Duplicacy*. HOWEVER, I didn’t change permissions on any files (and nor is it a good idea to either, since you don’t want to reset inheritance on a user’s profile). Since .\Duplicacy is part of the Administrator(s) group (note the ‘s’), it backs up the user account just fine. (Although I believe there’s a situation - perhaps on Windows Home - where you can create user accounts and lock it down, removing Administrators, but I don’t think that’s a default configuration; regardless, I use Pro.)
On one of our client’s workstations, we installed it as a service for all users with the default SYSTEM account. Here, it’s backing up the whole of C:\Users successfully without fiddling with permissions.
These are junction points - they point to other areas that already exist in the user’s profile. There’a about 12 of them, and they’re there mainly to support backwards compatibility with Windows 7 style locations. Don’t delete them, you can safely ignore the warnings, or exclude them from being backed up.
Problem solved? 
* Edit: The reason for having a custom account is solely so it can access a network share on a Windows Server - with corresponding account name and password. Unfortunately, the new Samba backend isn’t very reliable for me, so I’m using old style UNC paths… reminds me, I need to file a bug report for that. 



